We do BSA (Business Software Alliance) Assessments, to ensure that our clients are ready for the BSA compliance audits. Aside from that, we have also performed assurances and audits based on Bank Negara’s GPIS1 security guidelines and Security Commissions’ security and project requirements.
Our software licensing assessment methodology is as follows:
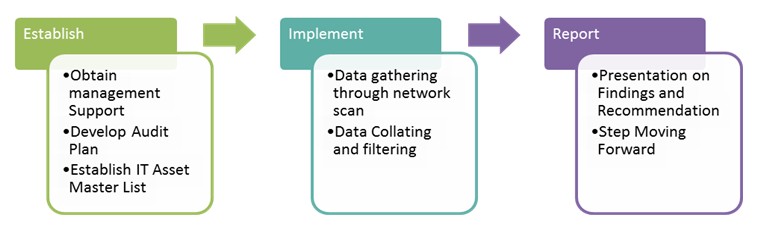
The assessment will include offsite and onsite work, with preparation required for documentation done on the client side. The team of certified information systems auditors will then verify with evidence. We have also developed an asset scanner along with our R&D team in international, used mainly as an asset identification and inventorisation tool for organisations. This is a subset of our larger asset management audit program. In order for us to shorten our project time and cost, we request the following checklist to be filled and be prepared, so that the team can immediately start the scan process:
1) List of purchased software with its license key and owners
2) List of purchased laptop/computer/server and its owners
3) A new administrative account with password protection on all laptop/computer/server for PKF Consultant audit purpose.
4) List of freeware that are authorize by the organization
5) Any policies and procedures related to software acceptable use.
6) Evidence of software purchase if any
7) List of restriction for PKF consultant to follow if any.
Customer Assessments
In 2004, Bank Negara (Malaysia’s Federal Bank and Regulator) instituted their Guidelines on Management of IT environment (or GPIS1). The areas we assess includes IT management and oversight, System security, System Development, Operations, Network and business continuity and contingency. We have mapped each requirement of GPIS1 out to corresponding control objectives under COBIT as well as ISO27001 standards.
We have also been called to perform assessments with requirements specifically from Securities Commissions, whereby, based on these requirements, we break down to map to objectives listed in either COBIT, ISO27001 or even PMBOK (Project Management Body of Knowledge), depending on the type of assessment required. An example will be a specific mapping below. Based on the objectives, we define the standard used, and control areas. We then break into control objectives and then audit the implementation and documentation of the company based on these control objectives (evidence gathering).
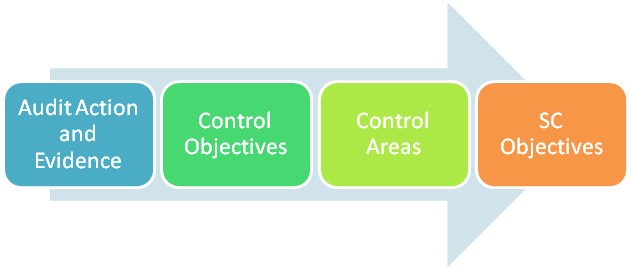
Further example will be as follows:
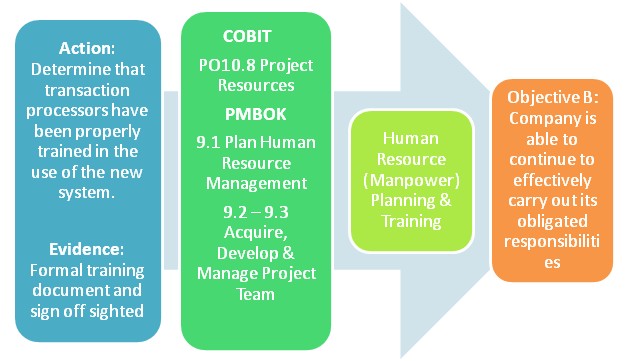
In this case, the result will be quantifiable and reference will be very clear to which portion the control is being assessed against. We then plot the result against a defined maturity index published by ISACA, the governing organisation for information security audits, in their “IT Assurance Guide Using COBIT, Appendix VII—Maturity Model for Internal Control”, that provides a generic maturity model showing the status of the internal control environment and the establishment of internal controls in an enterprise.
Call us at +603 6203 1888 or email avantedge@pkfmalaysia.com for more details or promotional pricing for the packages.
Leave a Reply