There is a country song that goes:
I’ve never been the kind to ever let my feelings show,
And I thought that being strong meant never losin’ your self control
But I’m just drunk enough, to let go of my pain,
To hell with my pride, let it fall like rain, from my eyes,
Tonight I wanna cry.
And cry they did. Almost 75,000 and counting, over 99 countries hit by one of the largest ransomware attacks of all time, “WannaCry” and the other Wanna* variants.
Wannacry was released on the 12th of May 2017. The irony of it all was that we were invited as one of the speakers in a Ransomware event in Putrajaya under Panda Security the day before and we were just warning those in attendance that the next wave of ransomware is due to hit and within 24 hours, bam, we have Wannacry. In Malaysia, there seems to be already infection, thanks to the guys at
https://intel.malwaretech.com/botnet/wcrypt/?t=24h&bid=all
There have been reports of large telecommunication companies, banks and telcos are being affected. Tens of thousands of networks worldwide have been hit and the attacks do not appear to be targeted to any specific region or industry. Once infected, victims are asked to pay approximately $300 by Bitcoin. For the curious, you can check
https://bitref.com/13AM4VW2dhxYgXeQepoHkHSQuy6NgaEb94
This means there is around 5.8348 bitcoins paid already to this. Which translates to around RM46,000 paid so far – which isn’t so much if you think the average of ransom payment is around RM10,000 – RM11,000 for other ransoms.
So what is this?
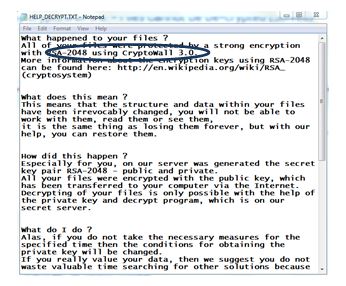
Wannacry is using the file extension .wncry, and it also deletes the Shadow Copies (which is normal for ransomwares, like Locky) which is a technology introduced into the Microsoft platforms as far back as Windows XP and Windows Vista as the Volume Shadow Copy service. This means that even backup copies produced by this service, such as Windows Backup and System Restore will be screwed. That’s mean. Here is the command executed.
cmd.exe /c vssadmin delete shadows /all /quiet & wmic shadowcopy delete & bcdedit /set {default} bootstatuspolicy ignoreallfailures & bcdedit /set {default} recoveryenabled no & wbadmin delete catalog -quiet (PID: 2292)
The following file is also created in the affected systems: @Please_Read_Me@.txt
How it gets in is just like any other ransomware: email either phishing or spear phshing. Basically, don’t click on any email attachments that are suspicious! It’s easier said than done, especially if you see one coming in stating that you are behind in your payments for your credit card. Resist the urge. One of the things to check on email:
The return email – most phishing doesn’t even attempt to spoof their email, and you will get emails coming from strange domains like maaybank or clmbclicks. Bad language is also a hallmark of a phishing email. “All your base are belong to us” type of english. Anyone asking for passwords, or click on a link etc is nonsense. Don’t click on email links. Don’t click on the attachments, above all.
Back to Wannacry. It exploits a known Microsoft Windows vulnerability to spread. This vulnerability was released as part of the Shadow Brokers leaks back in April. It hits the SMB (Server Message Block) – some people pronounce it as SAMBA, which technically is not so correct, as SAMBA is the SMB implementation on Linux. It basically allows the sharing of files and printers in networked environment. Which means, if one gets infected, the infection spreads through network shares even to systems without connectivity to the internet.
Microsoft released a patch for MS17-010 on March 14th 2017. Obviously, a lot of systems – especially those in healthcare still runs on Windows XP. The case has been deemed so serious that Microsoft has taken the step to release patches for systems already dead like XP! This shows how unusually dangerous this ransomware is.
OK, so if you have been hit, what do you do?
Well, you can pay. Around 41 transactions have been made so you could make the number, but don’t expect too much out of it. In fact, we probably do not recommend this course of action. You need to remove Wannacry and there are plenty of sites that gives details on that. The problem with ransomware is not so much of removing it, its a matter of recovering your files. Here’s a site you can check if there is a decryptor available:
https://www.nomoreransom.org/crypto-sheriff.php
Please be careful – some so called ‘decryptors’ are disguised as further malware and gets you a double whammy of sorts, so you need to ensure these are proper tools and not something you download from torrent.
As an advisory to all our clients, especially PCI-DSS here’s what you can do to protect yourself:
a) PATCH
https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
Now we see how important it is to patch your systems. Most PCI clients struggle on this and the examples can come from: Our servers are not connected to the internet, or If I patch, my application breaks. Well, if your application breaks then you need to get a warranty from your developers or get them to upgrade and improve.
b) Backup
While PCI doesn’t really focus much on backup or BCP (after all PCI’s interest is in the confidentiality of credit card and not the availability of your business) – it’s still good practice to backup your system. And not just online as ransomware hits shadow copies firstly – but offline backup and ensure your restoration has been tested. Remember those grandfather-father-son backup scheme you learnt in college and university? Yup, it can be applied.
c) Antivirus and Antimalware Updates
While it’s known Antivirus is missing a chunk of malware out there, it’s still for many systems the last line of defence and most vendors have released protection signatures for the ransomware so get it updated. It’s like having the final militia protecting against an invasion. It will probably not hold out forever, but at least it buys your administrators some time.
d) Remove SMB v1 support
Simply, for Windows 8 for instance, you need to run Powershell in administrator mode and then just issue
Set-SmbServerConfiguration -EnableSMB1Protocol $false
to disable SMBv1
e) Network segmentation
While this is helpful, it still doesn’t save everyone. Segmentation helps because it isolates computers. Vector of attacks usually comes into the access network (where end users access) and if you segment this from the critical systems, you will need the malware to traverse through your firewall or a filtering device in between which leads us to:
f) IDS, SIEM, IPS or any protection systems you have!
If you don’t have any IDS, IPS or SIEM deployed in your environment, it’s time you get one and this is a good argument for your business budget. IDS/IPS are usually available features in most firewalls these days, so if you segregate your networks, you can then enable these features and it should detect or prevent malware coming into your critical environment.
SIEM is critical. Security Information and Event Management systems have been around since the dawn of time but most companies avoid these due to costs, ever relying on the good old free syslog services. No, not allowed anymore, as far as PCI is concerned. We need more visibility over these logs, malicious traffic and even outgoing traffic to check if there is any communications with a command and control (C&C) server, which is the normal operations of these ransomware. SIEM these days are also no longer that expensive, with a Gartner SIEM like Alienvault starting off at a little over RM25K to get it up and running. We recently deployed a very large SIEM deployment over AWS cloud and on-premise on a major airlines with a fraction of the cost compared to traditional SIEM deployments.
There you have it. WannaCry is a very serious outbreak and we will be monitoring this system and also making our visits to our clients to give a short talk and description over it. If you have any questions over this, or on PCI-DSS or SIEM, drop us a note at avantedge@pkfmalaysia.com.
Stay safe!