I generally store all my customers’ project data in folders and back them up on a weekly basis. May was crazy as it was the first time for everyone filing their GST with Customs Malaysia. To cut to the story, I was so busy that I didn’t do any backups for three weeks in a row. Guess what? I got attacked! An extremely bad case of internet intrusion that made me cried tears of anguish.
I was ‘googling’ for something that I was researching on and went into a website that looked ‘harmless’. My laptop was on Norton Antivirus Program. No alert or red flag went up but 10 minutes later, I couldn’t access any of Excel or Word docs. There was an additional notepad document in each of my folders. I knew I’ve been attacked right away.
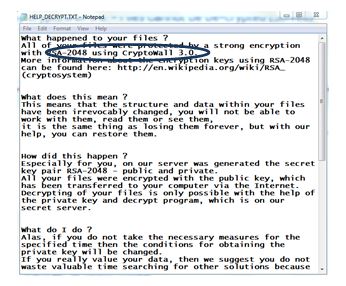
I opened the notepad to read the message – I need to know what virus I’ve been infected with to decide what my next move should be.
So, it’s Cryptowall 3.0. It’s one of the newer versions of ransomware and so far, no available ‘key’ available to decrypt. There are many others out there that have been decrypted by helpful forum-ers but not Cryptowall 3.0. They want money before my files can be decrypted. There’s never been proven that if you pay them, they would give you the key to decrypt the files and it is my belief that we should never encourage these people to bribe and threaten in this manner.
Rather than crying over spilt milk, time for me to assess how to restore and clean my laptop. This is what I did.
1) Restore
Restore from my backups that were three weeks’ ago. Unfortunately, the work that I had done after my last back-ups was a lot. Not good. However, Microsoft does have feature that is very useful – ‘Restore Previous Version’
If you right-click on each folder, there is an option to select the restoration date of your folders. It is a life saver in many ways – you may not get your latest but it saves you tons of hours of trying to figure out what you done on your documents for the past three weeks – in my case. So, it was an ardous task of right-clicking on ALL my folders and restoring them to the so-called ‘latest’ version.
 2) Anti-virus program re-assessment
2) Anti-virus program re-assessment
Many times, it could be our own fault that we don’t update the latest virus update. In my case, it is auto-updated. So, go figure. I checked that I was still on auto-update mode for the program but the virus attacked anyway. We need to know that t here are no virus-proof programs. Hackers come up with new viruses on a daily basis. If you visit AlienVault’s OpenTreatExchange (OTX) forum; the viral list grows everyday. It is to our own benefit to be preventive rather than reactive when it comes to being on the alert and to ensure that we have a reasonable Internet Security Application in place of work.
3) Cleaning up my laptop
For those not in the know, there many forums available for poor ‘infected’ souls like us, who are willing to help clean up and make sure our laptops are running back in tip-top condition. It would be very foolish ( I repeat, foolish) to not do a proper clean-up after being infected as you may risk your files being encrypted again. Using Norton to clean-up is probably the bare minimum you should do; however, I wanted to be very sure. Speaking of forums, I have always gone to two forums which has helped me answer questions about all sorts of stuff about Internet Security & etc.
a) http://www.bleepingcomputer.com
b) http://forums.whatthetech.com/index.php?showtopic=129712&hl=
In my case, I decided to go to whatthetech. If you are a registered user of any of these forums, they will go through each step to help you. You can view my thread on how the clean-up process went from the link I’ve provided. No obligation to pay but donations are most welcomed by the folks that dedicate their time on the forums. (This article is not paid or asked by whatthetech).
4) Some things to take note
• Avoid P2P file sharing programmes; they are a security risk which can make your computer susceptible to malware. File sharing networks are thoroughly infested with malware – worms, backdoor Trojans, IRCBots, and rootkits propagate via P2P file sharing networks, gaming, and underground sites. Users visiting such pages
may see innocuous-looking banner ads containing code which can trigger pop-up ads and malicious Flash ads that install malware. The best way to reduce the risk of infection is to avoid these types of web sites and P2P programmes
• Registry cleaners and optimization tools that claim to speed up your computer should be avoided, and are potentially dangerous. By running a registry cleaner you risk rendering your machine unbootable.
• Personal Data Sharing: Wild Tangent Games – Did you know that if you own an ACER laptop/desktop, Wild Tangent Games are PRE-INSTALLED? Apparently, ACER has a partnership with them. What you need to know is:-
The privacy policy of Wild Tangent Games; by default, will indicate that you had agree to advertisements by WildTangent, third parties and brand studies whereby you had allowed WildTangent Games to collect certain personal information.
This was discovered by whatthetech consultant that was helping me. So, if you own an ACER laptop, beware and uninstall all Wild Tangent Games. [Check out my piece about Personal Data and PDPA Malaysia – http://www.pkfavantedge.com/pdpa/the-iot-internet-of-things-my-personal-experience/]
5) Back-up Frequently
Back-up, Back-up, Back-up. I cannot emphasize the importance of this exercise. Back-up at least once a week; especially if you have done a lot of work that week. You may choose to back-up your personal and work items separately in terms of frequency, but back-up all your precious memories and work.
My viral attack drama ends here. I certainly do not wish this drama on anyone.
Be SAFE!!!
For Internet Security Applications advisory or PDPA training, drop us an email at avantedge@pkfmalaysia.com or contact us at +603 6203 1888.
by Agnes Yew, PKFAE Project Manager

Leave a Reply