
All good things must come to an end.
Over the weekend, AT&T put an official announcement out to all partners what we have been informed weeks earlier, that the Alienvault Appliance has now got an expiry date in terms of its life. Since we picked up Alienvault six years ago, dealing with the small support team out from Spain and sales team from Cork, Ireland, it has been a good ride and we’ve learnt massively a lot through the years. AT&T is steering into a different direction, and Alienvault is moving completely into cloud, putting an end to the ever popular All-in-Ones and Standard Appliance. We will miss the days of writing plugins for our clients.
Anyway, here is our official announcement:
27th September 2021
Alienvault USM Appliance End of Sales (EOS) and End of Life (EOL) Announcement
There has been an official announcement from AT&T to all channel partners dated 25th September 2021, that the Alienvault USM Appliance will be placed on a new sales hold effective January 1, 2022. AT&T will also no longer support the USM Appliance effective January 1, 2025. These dates are effectively the End of Sales (EOS) and End of Life (EOL) dates for the USM Appliance (otherwise known as Alienvault On-Premise). If your solution is an “All-in-One”, “USM Standard” or “USM Enterprise”, these solutions will be the ones affected by this announcement.
As one of the first partners of Alienvault in Malaysia since 2015, we are saddened with the news that the popular USM Appliance solution will no longer be available from 2022 onwards. We therefore require any new sales made (either from us or from our partners) from now till 31st December 2021 to inform the potential customer of the above EOL and EOS dates to ensure that purchases are made with this information clearly stated. This is to avoid any miscommunication of expectations to the end-user. Additionally, we will cease all local maintenance support renewal from the date of this letter. The local maintenance support includes arrangements for 24×7, or 8×5 call or onsite support from PKF directly. We will continue to honour all ongoing contracts until the contract expiry. This is in line with us re-allocating our technical resources and focus to other solutions and initiatives. The annual maintenance support and threat intelligence subscription from AT&T will still be continued until 31st December 2024. PKF will still be continuing our quarterly preventive maintenance or any ad-hoc professional service to assist our clients on USM Appliance matters. In summary, the cease dates are as follows:
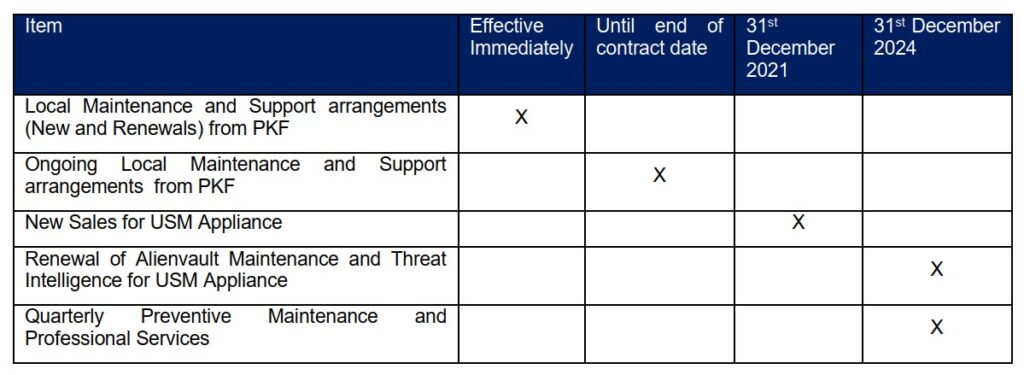
As we move our focus away from the USM Appliance in both sales and support, we would recommend a transition plan to be in place. This can include the option to move to USM Anywhere, which is the direct transition to AT&T’s SaaS based SIEM. Please contact us at alienvault@pkfmalaysia.com for further details in moving forward.
Thank you for your support all these years and we hope that we can continue to work together for many years to come.


