With the rapid advancement in information technology, businesses are moving to an intensive IT-integrated model. By utilizing the features of information technology, businesses are able to reach out to more audiences, regardless of geographical aspects and language barriers. This provides an advantage to business; higher audience in a relative lower costs. However, the utilization of information technology is a double-edge blade, as confidential information are stored as data in servers available in the internet, as compared to printed hard copies of documents kept and locked in cabinets.
To ensure continuous availability of information, the network the server resides is connected to an untrusted network, namely the Internet. In order to protect unauthorised access to the information, security measures are needed to be implemented. In this article, we will discuss about the firewalls and intrusion detection systems.
Difference between Firewall and Intrusion detection system
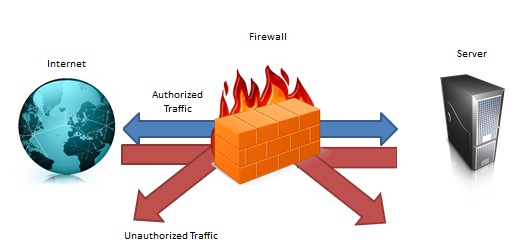
A firewall is a device or group of devices that enforces an access control policy among networks.” Its main function is to control incoming and outgoing traffic, between two networks by allowing and denying such traffic depending on pre-determined rule sets. Therefore, a firewall is a preventive control acting as keys and locks between the networks, as shown in figure 1 below:
An Intrusion detection system (IDS) on another hand, is a device or application that monitors network activities and attempts to detect suspicious activities going through the network. Consider IDS as a burglar alarm for your office; when they enter your office (i.e. unauthorised access), the alarm will alert you. Therefore, IDS is a detective control; its main function is to warn you of suspicious activity taking place ? not prevent them (Refer to figure 2):

Reason for IDS
A firewall is a crucial component of securing your network. The predefined rule set within the firewall provides protection that any traffic going through the closed ports are denied but also allows some of these through the network as well. However this means that the access allowed is just let through, and firewalls have no clever way of telling whether that traffic is legit and normal. This is where IDS comes into play.
Placed between the firewall and the system being secured, a network based IDS can provide an extra layer of protection to that system. For example, monitoring access from the internet to the sensitive data ports of the secured system can determine whether the firewall has perhaps been compromised, or whether an unknown mechanism has been used to bypass the security mechanisms of the firewall to access the network being protected.
Let’s take a look at an example by referring firewalls to locked doors (key and locks) and IDS to alarm systems (as mentioned above). Let’s say that you have lots of confidential documents stored in a filing room within your office: The locked doors will stop unauthorized individuals from entering the filing room. By themselves, they do nothing to alert you of an intrusion, but they deter unauthorized access. The alarm system will alert you in case an intruder tries to get into the filing room. By itself, it does nothing to prevent an intrusion, but it alerts you to the potential of an intrusion. As you can see, both security mechanisms complement each other, providing better overall security towards the access of such confidential documents.
It should be noted that IDS should not be employed as a single security mechanism. By using a layered approach, or defence in depth, a network should have multiple layers of security, each with its own function, to complement the overall security strategy of the organization.
Conclusion
Before implementing security controls within the organisation, it is crucial to conduct a risk analysis based on the confidentiality, integrity and availability of the data. As there are almost no servers that are immune to penetration/intrusion, it is recommended that the security mechanism implemented are capable of minimizing the risk.
In the next article, we will talk about Intrusion Prevention System and the reason for having one within an organisation.
Leave a Reply