Some of the building blocks in a risk assessment is the identification of threats and vulnerabilities. A lot of times, many people do get mixed up between these two. In the context of ISO27005, a risk is typically defined as the potential that a given threat will exploit the vulnerabilities of an asset or group of assets, causing harm to the organisation. So, understanding both threats and vulnerabilities is crucial to effective risk management.
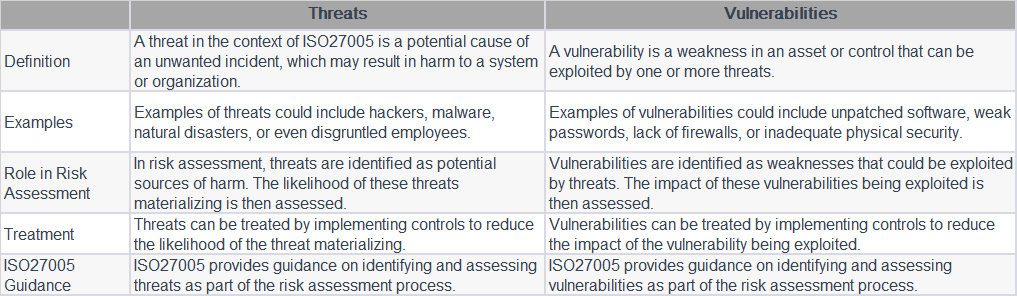
The above table provides a typical understanding of the difference between these two.
Now, let us provide a few examples of threats and vulnerabilities that you may find useful when you are deriving these for your risk assessment.
a) Database Threats and Vulnerabilities
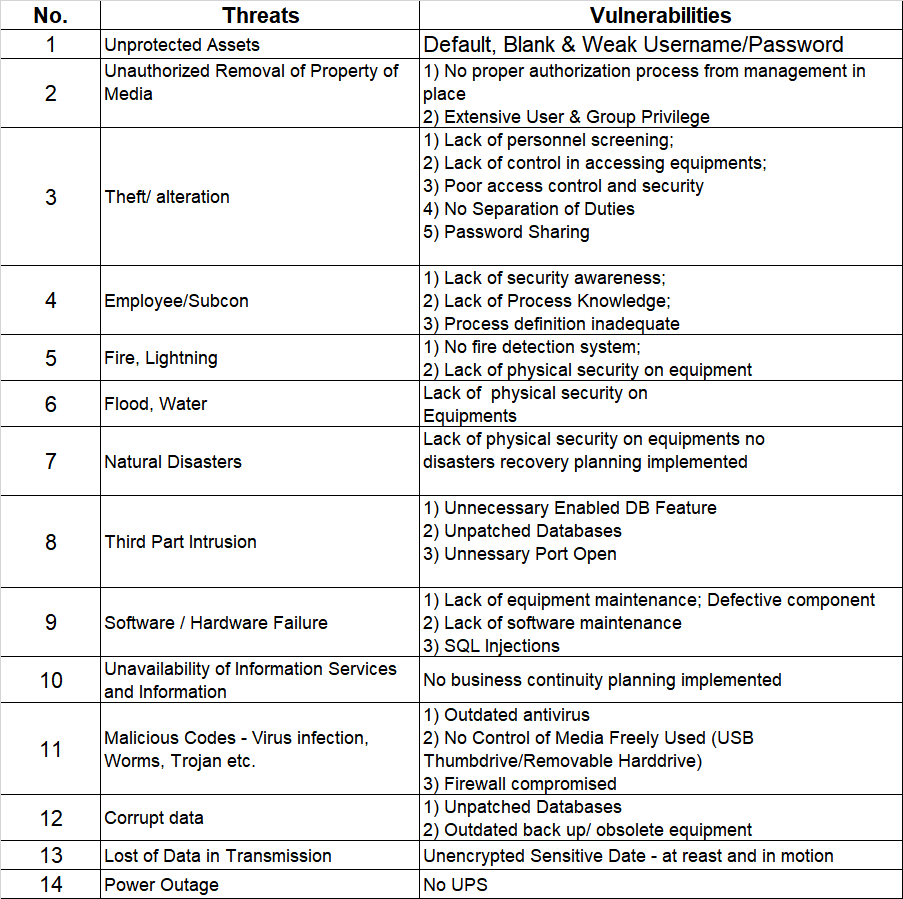
b) Servers Threats and Vulnerabilities
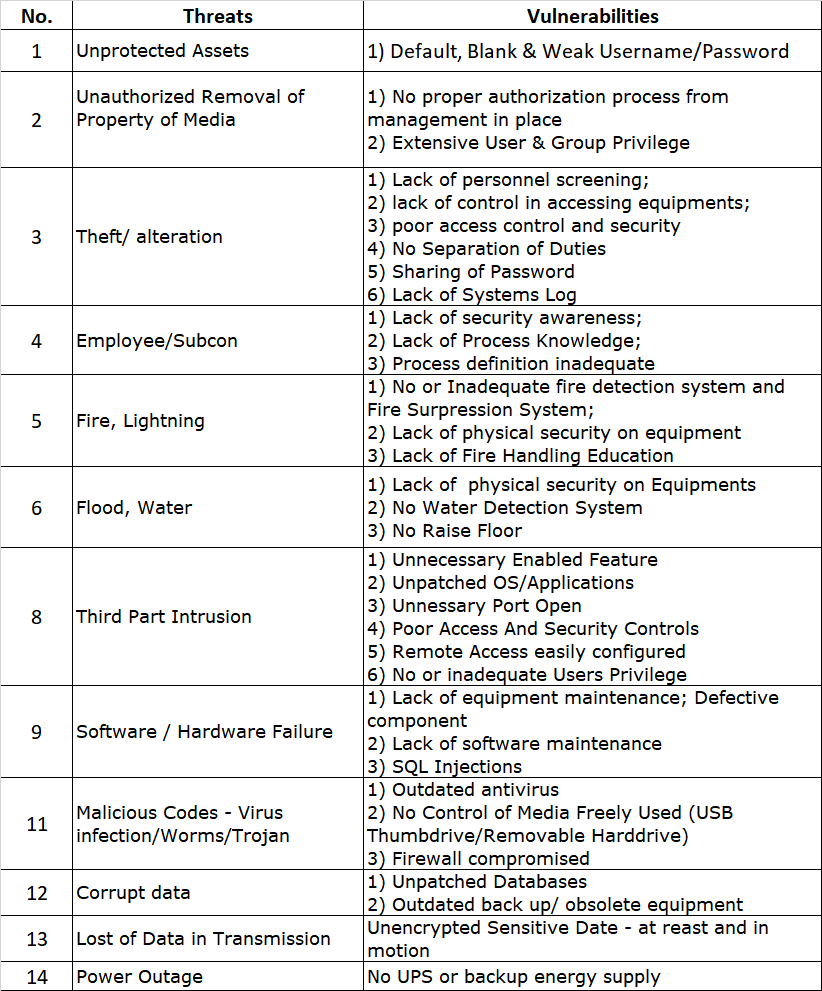
c) Physical Environment Threats and Vulnerabilities
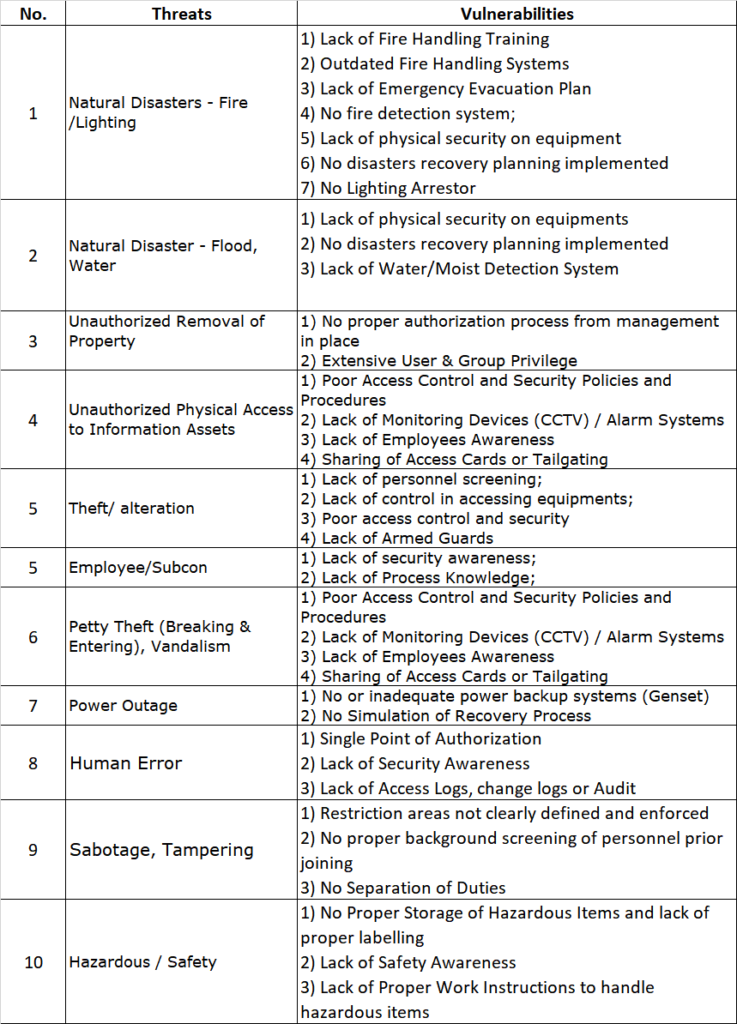
d) Documentation Threats and Vulnerabilities
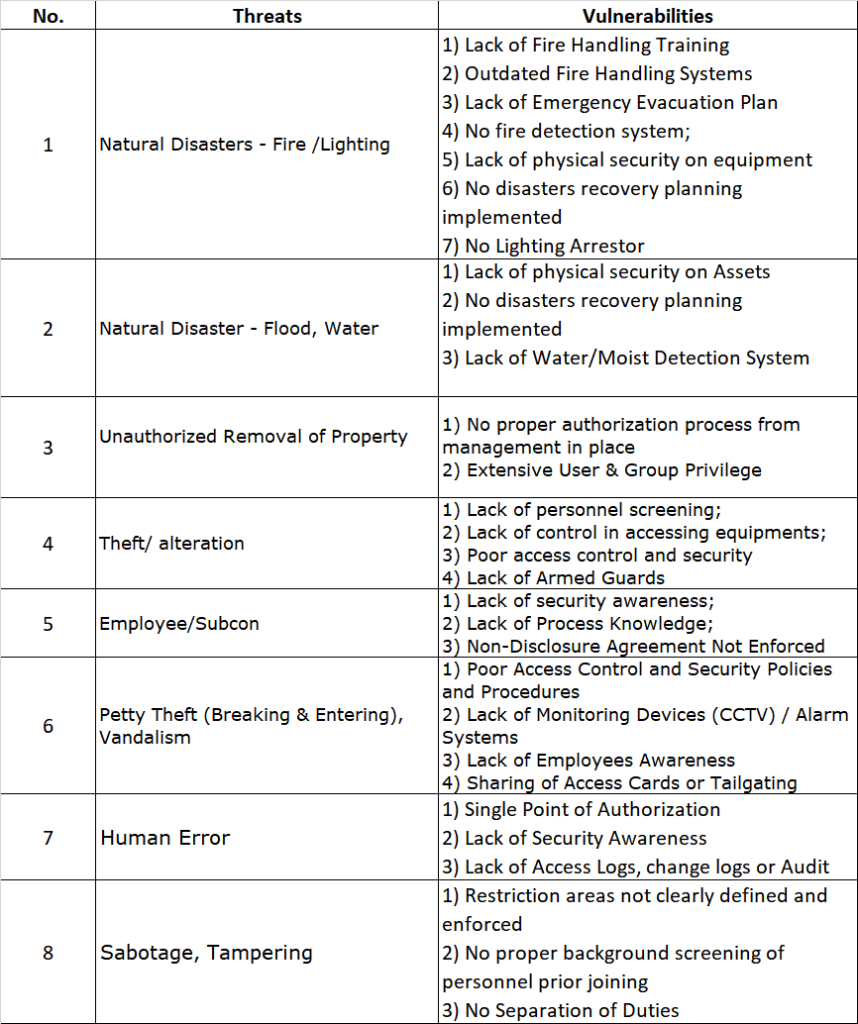
e) Application Threats and Vulnerabilities
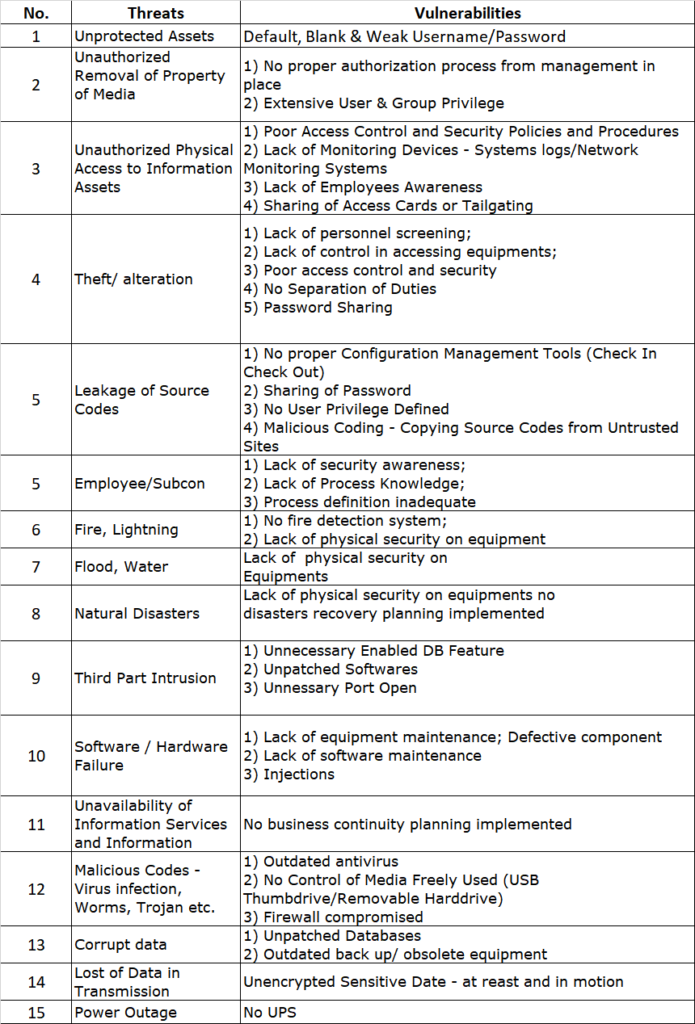
f) HR (Employee) Threats and Vulnerabilities
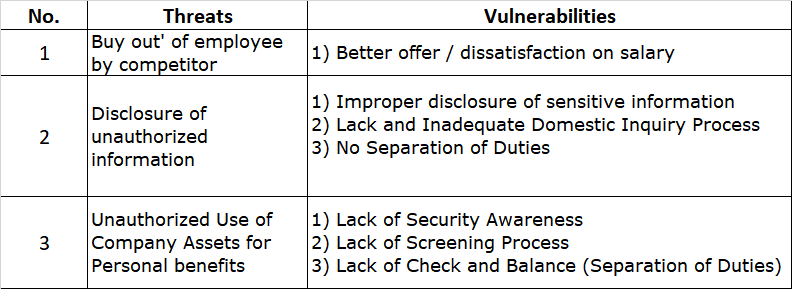
The above are samples and examples. There could be many many more different threats, categories and vulnerabilities that are identified in the context of your organisation. If you need any assistance, please let us know and drop us a note at avantedge@pkfmalaysia.com.
Leave a Reply